By
Ron B.
Dec 22, 2025
Education
Vaults Executing Yield-Bearing Strategies
These vaults accept deposits and generate yield through lending, staking, or liquidity provision. All follow the ERC-4626 standard, but strategies range from simple to highly complex. Examples include Upshift's upUSDC and hgETH vaults.
How They Work
Tactical approaches scale in complexity. On the simple end: single-asset lending—deposit USDC into Aave, auto-compound interest. On the complex end: leveraged loops, delta neutral positions, cross-protocol strategies.
The difference matters because NAV calculation complexity scales with strategy sophistication.
Two Examples Show the Scaling
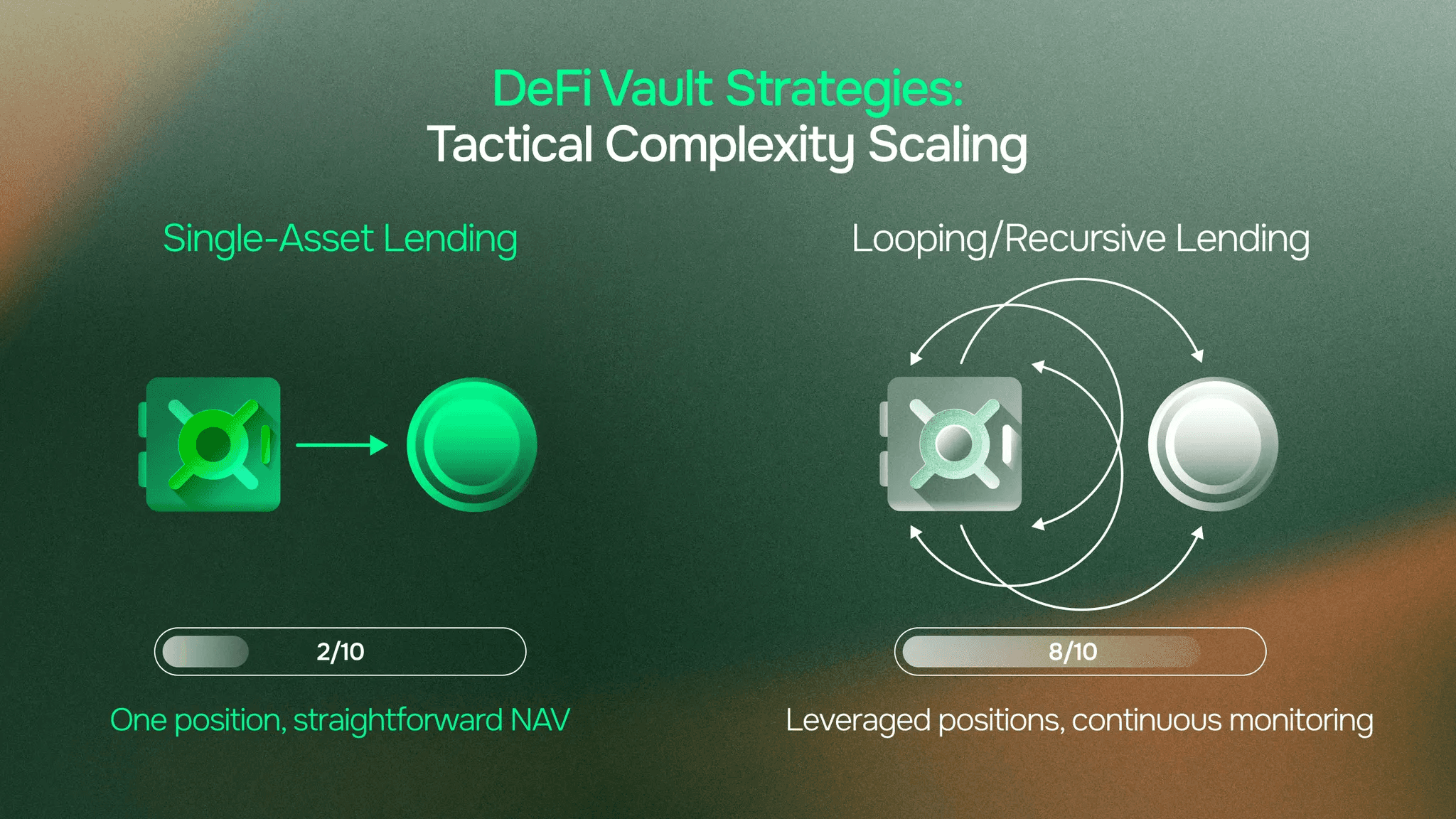
Single-Asset Lending (Simple)
A vault deposits USDC into Aave. Receives aUSDC—a rebasing token where your balance increases as interest accrues. Week one: 1,000 aUSDC. Week two: 1,005 aUSDC. The yield appears directly in your balance.
NAV calculation here is straightforward. Track one position. Account for rebasing mechanics. The vault's total assets equal its aUSDC balance converted to underlying value.
Oracle needs? Minimal external dependency. Mostly on-chain calculation. The lending protocol's own oracle determines collateral valuations, and the vault inherits that infrastructure.
Looping/Recursive Lending (Complex)
Now consider a vault executing a leverage loop. Deposit wstETH as collateral. Borrow WETH against it. Convert borrowed WETH to wstETH. Redeposit as additional collateral. Repeat until reaching 3x leverage.
This creates a recursive position where the vault simultaneously holds collateral and debt. The NAV calculation must track both sides, monitor the health factor continuously, and account for changing values across multiple layers.
Oracle needs? Real-time accurate collateral valuation becomes critical. A 2% error in reported wstETH price cascades through leveraged positions. What looks like a safe 300% collateralization ratio might actually be 290%, triggering liquidation.
Health factor monitoring requires constant updates. Rebalancing triggers depend on accurate position data. Small oracle failures become large problems when leverage amplifies exposure.
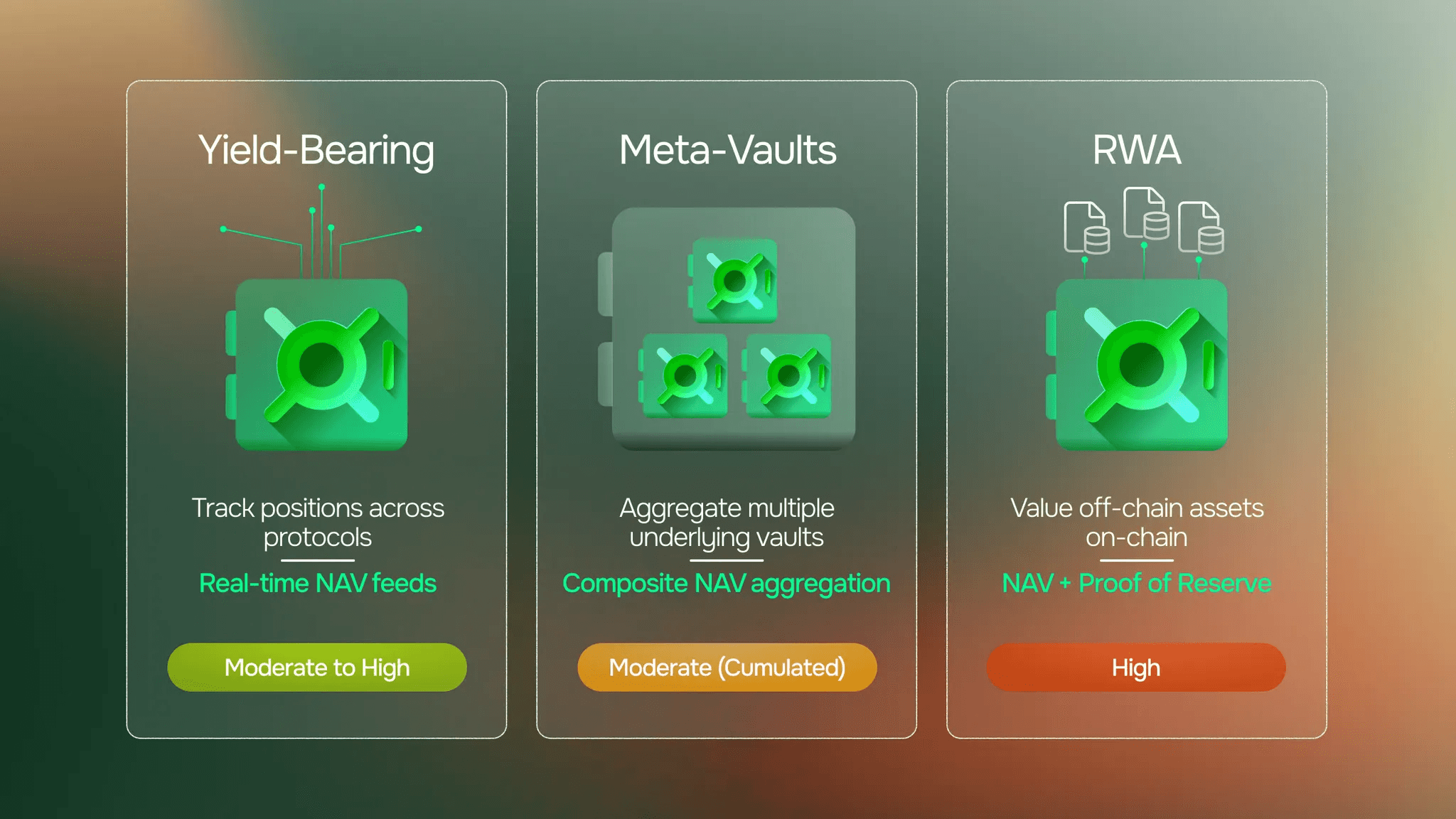
Oracle Requirements for Yield-Bearing Strategies
Here's what this strategy category needs:
NAV feeds that price vault tokens. The formula is simple: Total Assets ÷ Total Supply = NAV per share. This NAV per share IS the vault token price. Not market price from trading, but calculated value from underlying positions.
Token accounting complexity. Yield-bearing vaults often hold diverse positions. Aave's aTokens (rebasing). Compound's cTokens (non-rebasing, exchange rate increases). Same vault, different mechanics. NAV infrastructure must abstract this complexity, providing unified valuation regardless of underlying token type.
Real-time yield tracking. As positions accrue value, NAV updates dynamically. For simple strategies, updates might be infrequent. For complex strategies involving leverage or delta neutral positions, real-time becomes critical.
Operational parameters. Complex strategies need more than just valuation. Health factor monitoring tells the vault when it's approaching liquidation. Rebalancing triggers signal when to adjust positions. Automated risk management depends on accurate, timely data.
Composability data. Other protocols consuming vault tokens need verified NAV. A lending protocol accepting vault shares as collateral must know current value. Without reliable data, composability breaks down.
Why Generic Price Feeds Fall Short
Generic oracles are designed for spot prices. ETH/USD. USDC/DAI. Simple market prices from trading activity.
Vault tokens don't work this way. Their value derives from underlying positions across protocols. There's no "market price" to observe. You must calculate value from the vault's holdings.
Generic price feeds also don't understand vault mechanics. They can't track rebasing tokens versus non-rebasing. They don't know how to aggregate multi-protocol positions. They weren't built for this.
Oracle Risk Context
Risk severity varies by tactical approach. Simple single-asset lending: Moderate. The vault inherits whatever oracle risk exists in the underlying lending platform. If Aave's price feeds are reliable, the vault is reliable.
Looping and recursive strategies: High. Leverage amplifies errors. A vault operating at 3x leverage with a 5% oracle error faces a 15% position error. Small data problems become large losses quickly.
Delta neutral strategies: Very High. These pair spot positions with perpetual shorts to capture funding rates. Both legs need synchronized pricing. If the spot oracle and perpetual mark price diverge even slightly, the hedge breaks. What looked risk-neutral becomes directionally exposed.
Understanding your strategy's risk profile matters when choosing data infrastructure.
Vaults Executing Diversification Strategies (Meta-Vaults)
Meta-vaults allocate across multiple underlying vaults. Think fund-of-funds in traditional finance. One deposit, diversified exposure across different strategies and risk profiles.
Upshift's coreUSDC is an example: it diversifies across multiple stablecoin vaults, each with different approaches. The meta-vault curator rebalances allocations as market conditions change.
How They Work
Accept deposits, issue shares. The curator allocates capital across underlying vaults based on risk/return targets. Positions shift dynamically. One month: 40% in lending, 30% in LP strategies, 30% in stablecoins. Next month: allocations adjust.
Critical point: Strategies can change daily or more frequently. Oracle infrastructure must adapt dynamically. A meta-vault's composition today differs from yesterday. NAV calculation must reflect current reality, not stale allocations.
Oracle Requirements for Meta-Vaults
The aggregation challenge. Meta-vault NAV must reflect value of ALL underlying positions in real-time. Each underlying vault has its own NAV. The meta-vault NAV equals the weighted sum of underlying NAVs, adjusted for current allocations.
Sounds simple. Three underlying vaults? Manageable. Ten underlying vaults across multiple chains? Significantly more complex. Each component is a data dependency. Each dependency is a potential point of failure.
What's needed:
Composite NAV feeds that aggregate multiple underlying vault positions. Not a single data source. Multiple sources combined with appropriate weighting.
Multi-source data tracking positions across different protocols and chains. If the meta-vault holds positions on Ethereum, Arbitrum, and Base, the oracle must aggregate across all three.
Transparent methodology where calculations are independently verifiable. Other protocols need to trust not just the final NAV number but understand how it was derived.
Flexible updates as allocations shift. When the curator rebalances, moving 10% from vault A to vault B, NAV calculation adjusts immediately. The infrastructure must handle frequent compositional changes.
Complexity Scaling
More components mean more complexity. A meta-vault with three underlying positions is relatively simple. Add cross-chain allocations and the data aggregation challenge multiplies. Bridging data across networks introduces latency and verification challenges.
More data sources also mean more potential failure points. This is why risk severity for meta-vaults is Moderate (Cumulated). Not as severe as highly leveraged strategies, but the aggregate risk across all components adds up.
Oracle Risk Context
Meta-vaults inherit oracle risk from every component vault. If one underlying vault's data feed is compromised, the meta-vault's NAV becomes unreliable proportionally.
Consider a meta-vault with ten components. Nine have perfect oracle infrastructure. One has self-reported, unverified NAV. That 10% allocation becomes a trust assumption undermining the entire structure.
Diversification reduces idiosyncratic risk, true. But it introduces systemic risk if components share oracle dependencies. If multiple underlying vaults use the same oracle network and that network fails, the meta-vault fails simultaneously across multiple positions.
This is why independent, verified NAV aggregation matters. Trusting each component's self-reported value doesn't work at institutional scale. Third-party verification across all components creates the trust layer that enables composability.
Blending RWA Complexity
Meta-vaults can include RWA components. A structure might allocate 60% to DeFi yield-bearing vaults and 40% to an RWA vault holding tokenized Treasuries.
This compounds oracle complexity. The infrastructure must handle both on-chain DeFi positions AND off-chain asset valuation. Different data sources, different verification methods, unified reporting. It's a preview of the challenge we'll explore in depth next.
Vaults Executing RWA Strategies
Real-world asset vaults hold tokenized representations of off-chain value. Private credit. Treasury securities. Real estate loans. Money market instruments.
Midas's mF-ONE vault holds tokenized private credit from Fasanara Capital. The vault's assets are performing loans and receivables that exist off-chain, tokenized for on-chain representation.
The fundamental difference: No on-chain price discovery. You can't check Uniswap to value a T-bill. You can't observe Curve pool depth for private credit positions. The vault holds claims on off-chain value that must be brought on-chain through data infrastructure.
This creates the most complex verification challenge in the vault ecosystem.
How They Work
An asset manager (Fasanara, in the mF-ONE example) originates and manages off-chain assets. Those assets are tokenized and held by the vault smart contract. The vault issues shares representing proportional claims on the underlying assets.
NAV reflects underlying asset performance. Loan repayments increase value. Interest accrual compounds returns. Defaults reduce assets. All happening off-chain, reported on-chain through data infrastructure.
Settlement cycles matter. RWA assets often require traditional finance settlement windows. T+1, T+2, sometimes longer. You can't instant-redeem a loan portfolio the way you can swap USDC for ETH.
Three Amplified Challenges
Challenge 1: Off-Chain Asset Opacity
How do you verify the vault actually holds what it claims?
A vault reports $150M in performing private credit loans. Lending protocols want to accept the vault token as collateral. But how do they verify those loans exist? That they're performing? That valuations are accurate?
The data doesn't live on-chain. Smart contracts can't query Fasanara's loan book directly. The verification challenge is fundamental: bringing trusted off-chain data on-chain in a way other protocols can trust.
Challenge 2: Institutional Requirements (Zero Trust Assumptions)
Regulated entities can't operate on trust assumptions. They need auditable data trails. Independent verification, not vault operator attestation. Real-time NAV that accounts for off-chain asset performance.
"Trust the vault operator" isn't institutional-grade infrastructure. Regulators require verification. Risk managers require verification. Lending protocols require verification.
The data infrastructure must satisfy both traditional finance's regulatory requirements (audited valuations, verified holdings, documented methodologies) and DeFi's composability requirements (on-chain delivery, trustless verification, real-time updates).
Challenge 3: Composability Requires Trusted Data
Without reliable NAV, RWA vault tokens remain isolated. Lending protocols won't accept them as collateral. Risk managers can't model exposure to assets they can't value independently. DEXs can't price them for trading.
Capital stays siloed. The promise of composability—using vault tokens across DeFi—breaks down without verifiable data infrastructure.
Oracle Requirements for RWA Strategies
RWA vaults need more complex infrastructure than other strategies.
NAV feeds reflecting off-chain asset values. This requires incorporating external valuations, audited reports, and custodial data. Not just on-chain calculation. Multi-source verification where independent data providers cross-reference valuations.
Proof of Reserve verification. Independent confirmation that claimed assets exist. For on-chain assets, this is verifiable cryptographically. For off-chain assets, it requires integrating with custodians, auditors, and asset managers.
Multi-source data aggregation. Single-source data creates single-point-of-failure risk. RWA infrastructure must aggregate across independent providers, creating redundancy and cross-verification.
Regulatory-grade reporting. Audited valuations. Verified holdings. Documented methodologies that meet regulatory standards. This isn't optional for institutional RWA vaults.
Computational infrastructure. Complex positions take time to value accurately. Midas mF-ONE's NAV calculation can take half a day or more. This isn't instantaneous price feeds. It's deliberate, thorough valuation of illiquid positions. The infrastructure must handle this computational complexity at scale.
Flexible updates. As underlying asset values change—loan repayments, market movements, defaults—NAV must reflect current reality. But RWA assets don't update continuously like liquid crypto. They update periodically as valuations are recalculated. The infrastructure must handle asynchronous updates while maintaining data integrity.
Why Generic Oracles Don't Work for RWAs
Generic price feeds assume on-chain price discovery. Tokens trading on DEXs or CEXs. Observable market prices aggregated across venues.
RWA assets aren't traded continuously on-chain. There's no pool depth to observe. No order book to aggregate. Valuation requires understanding the asset class itself.
How do you value a performing loan? You model cash flows, discount rates, default probabilities. How do you value a Treasury? You check market prices from TradFi venues, adjust for accrued interest. How do you value a real estate position? Appraisals, comparables, rental income analysis.
This requires specialized infrastructure designed for off-chain asset valuation, not just price reporting from trading venues.
Oracle Risk Context
RWA strategies carry High risk severity. Highest among vault strategies we've covered.
Why? Off-chain valuations with centralized updates create data integrity risk. You're trusting external data sources to report accurately. Assets aren't freely traded on-chain, so there's no arbitrage mechanism to quickly correct mispricing. If someone reports a bad valuation, market forces don't immediately fix it.
NAV calculation latency creates exploitation windows. If NAV updates once per day and asset values move faster, there's a gap between reality and reported values. In volatile markets, this gap widens.
Single-source risk exists if relying solely on the asset manager's own valuations. Who verifies the verifiers? Independent third-party verification reduces this, but the trust assumption remains higher than fully on-chain strategies.
Systemic contagion risk matters because RWA vaults often serve as collateral across multiple lending protocols. If the oracle fails and affects NAV reporting, multiple protocols face exposure simultaneously. The interconnected nature of DeFi amplifies individual failures.
The Data Infrastructure Solution
Purpose-built infrastructure addresses RWA complexity through several mechanisms:
Independent NAV verification where third-party calculators determine vault value from underlying positions. Not self-reported by the vault operator. Not simply passing through asset manager data. Independent verification.
Stake-secured accuracy where data providers risk slashed capital for bad data. Economic incentives align with accuracy. This is how decentralized networks maintain trust without centralized authority.
Multi-source verification with distributed validator consensus. Multiple independent nodes verify data before publishing on-chain. Cross-reference valuations across sources. Build redundancy into the architecture.
Real-time flexibility where vault strategies change daily or more and oracle infrastructure adapts dynamically. A vault shifts from Treasuries to private credit? NAV calculation methodology changes accordingly. The infrastructure handles this flexibility without breaking composability.
This is infrastructure designed for institutional-grade RWA vaults. Not retrofitted from simple price feeds. Purpose-built for off-chain asset complexity, regulatory requirements, and composability demands.
Oracle Risk Severity: Strategy Comparison
Risk isn't uniform across vault strategies. Understanding severity helps builders choose appropriate infrastructure and helps protocols set appropriate risk parameters.
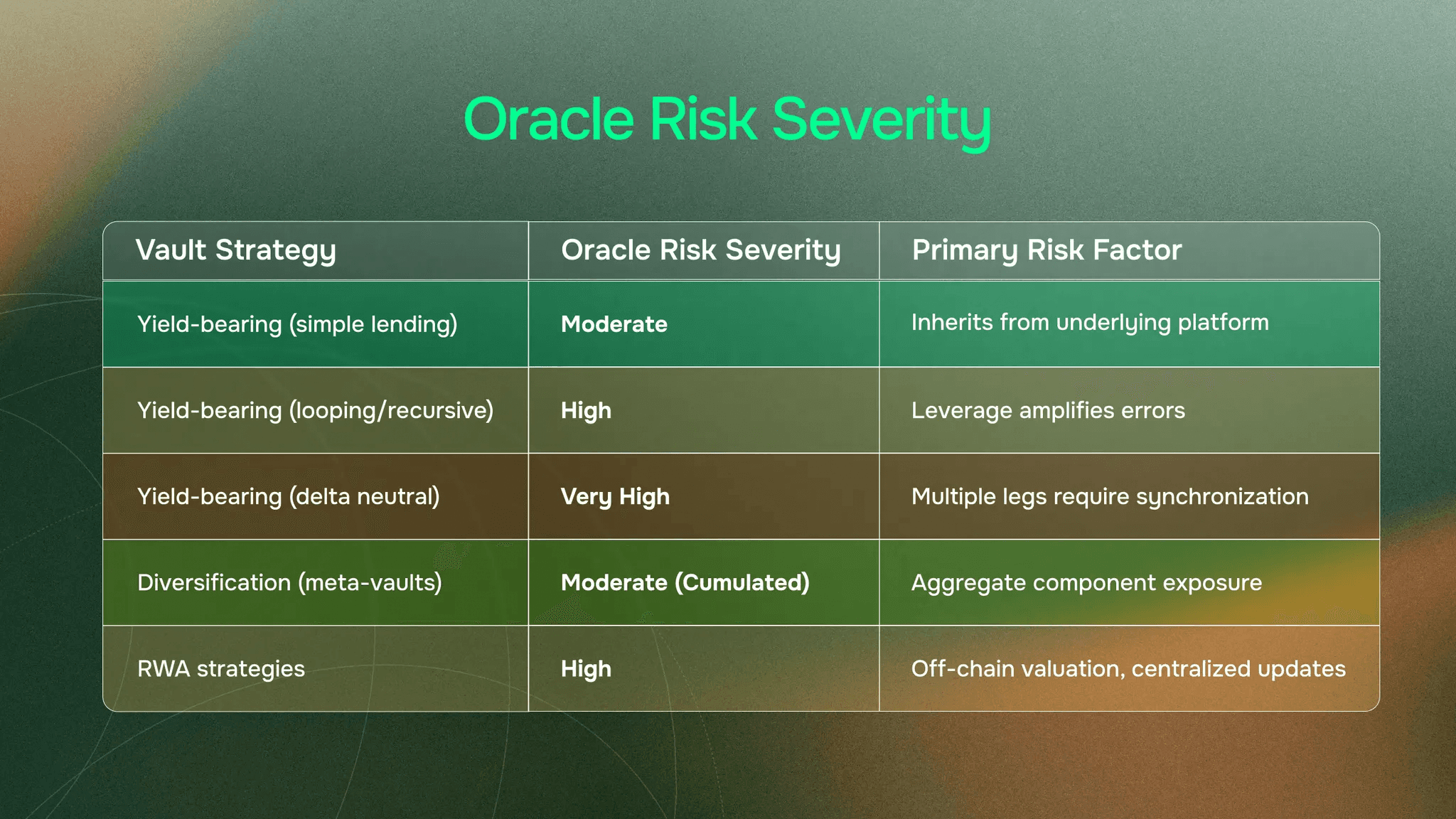
Complexity and leverage increase vulnerability to data issues. Strategies with higher risk severity require more robust oracle infrastructure.
For builders: understand your strategy's risk profile before choosing data infrastructure. For protocols accepting vault tokens as collateral: risk severity should inform LTV ratios and monitoring requirements.
This is why specialized, purpose-built oracle infrastructure matters. It's designed for the complexity and risk profiles of institutional vault strategies, not just simple spot price reporting.
Understanding Strategy = Understanding Oracle Needs
All vaults follow the ERC-4626 standard. Same interface. Standard methods. Interoperable by design.
Differentiation happens in strategy, not "type." And each strategy has fundamentally different data requirements.
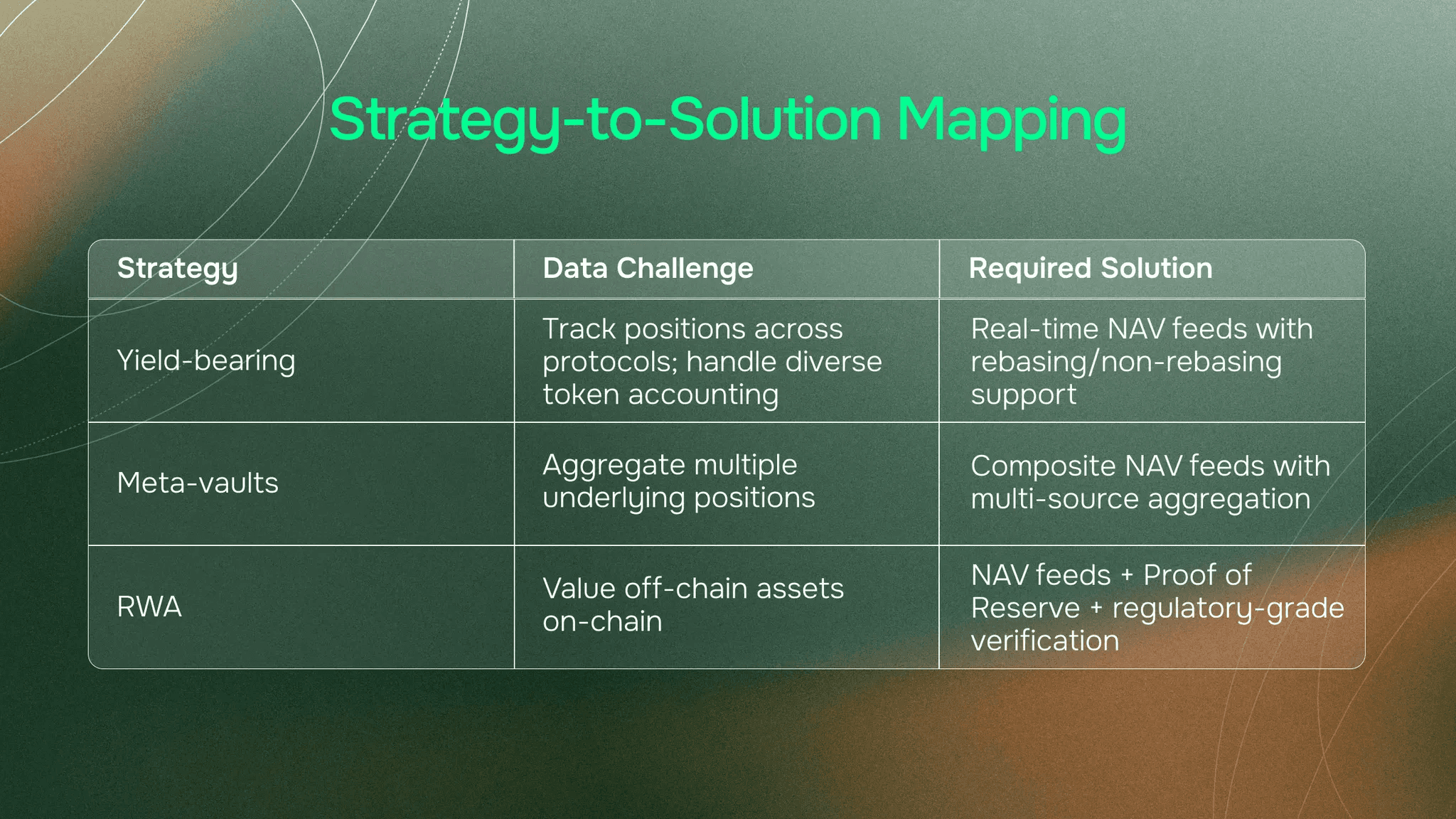
Critical infrastructure characteristics apply across all strategies:
Verifiability. Independent calculation, not self-reported. Third-party verification creates the trust layer that enables composability.
Flexibility. Strategies change frequently—daily or more in many cases. Infrastructure must adapt dynamically as vault positions shift.
Computational capability. Complex positions require time and infrastructure. RWA NAV calculations can take half a day. Leveraged strategies need continuous monitoring. The infrastructure must handle this computational load at scale.
Composability. The ultimate goal. Verified data enables vault tokens as collateral, tradeable assets, and DeFi building blocks. Without it, vaults remain isolated regardless of strategy sophistication.
For builders choosing oracle infrastructure: match the solution to your strategy's complexity. Generic solutions work adequately for simple strategies. They break down for complex, leveraged, or RWA approaches. Institutional adoption requires institutional-grade data infrastructure.
For protocols evaluating which vault tokens to accept: understand the oracle infrastructure behind the NAV reporting. Self-reported valuations carry different risk than independently verified, stake-secured data. Your risk parameters should reflect this difference.
Conclusion
Different vault strategies, different data needs.
Yield-bearing strategies vary by tactical complexity. Simple lending has moderate oracle requirements. Leveraged loops and delta neutral positions need robust, real-time infrastructure.
Meta-vaults face an aggregation challenge. Composite NAV across multiple underlying positions. More components mean more complexity.
RWA strategies require the most sophisticated infrastructure. Off-chain asset valuation, regulatory-grade reporting, Proof of Reserve verification. The intersection of TradFi requirements and DeFi composability.
As vaults evolve toward institutional scale and RWA integration, data infrastructure becomes foundational. Understanding what each strategy requires is the first step. Purpose-built infrastructure designed for vault complexity is what enables composability and institutional trust.
Explore EO Network's vault infrastructure: docs.eo.app
Next in this series: Deep dive on how NAV feeds work technically, From calculation to on-chain delivery.




