By
Ron B.
Dec 15, 2025
Education
Self-reported NAV worked when vaults held simple positions. When strategies became multi-protocol, that trust assumption broke. Now, with RWA vaults holding off-chain assets, the question isn't academic anymore: How do you verify what a vault holds when you can't check on-chain?
Three problems emerged as strategies evolved:
Self-reported valuations without independent verification
Off-chain asset opacity
Composability breakdown (protocols couldn't trust vault data)
We're at an inflection point. Infrastructure is catching up. Purpose-built oracle networks like EO Network now provide what vaults always needed: verifiable, real-time data that other protocols can trust.
This piece covers how vault strategies evolved and created new data requirements, why each strategy needs different verification approaches, and what purpose-built data infrastructure looks like for institutional adoption.
Phase 1: Simple Strategies, On-Chain Verification (2018-2020)
When strategies were straightforward and positions were entirely on-chain, verification was simple. On-chain calculations sufficed.
The Manual DeFi Era
Users chased yields across protocols manually. Every action required gas. Compounding was tedious and expensive.
Yearn changed this in 2020. Pool capital. Socialize gas costs. Auto-compound across protocols. The basket was simple: Compound deposits, Aave lending positions, basic Curve LP tokens.
Data Infrastructure: On-Chain and Simple
Vaults calculated APY on-chain. "We're earning 5% on Compound" meant checking Compound balance. Basic arithmetic. Smart contracts could query other smart contracts directly.
Why it worked:
Positions were entirely on-chain. All data lived on the same blockchain. Calculations were straightforward. Users could verify independently by checking the same on-chain sources.
No specialized oracle infrastructure needed yet. When everything lives on one chain and strategies are simple, smart contracts can handle verification internally.
No composability yet:
Each vault was custom-built. No standard interface existed. Other protocols couldn't easily integrate them, but that wasn't the priority yet.
Multi-chain strategies and off-chain complexity changed this equation entirely.
Phase 2: Multi-Protocol Strategies Outpace Data Infrastructure (2020-2021)
Strategy complexity exploded. Data infrastructure didn't. The gap created real problems.
Strategy Explosion During DeFi Summer
Mid-2020: protocols distributed governance tokens as incentives. Multi-step strategies emerged overnight.
Deposit DAI, farm Curve rewards, earn CRV, sell rewards, compound the position. Leverage loops across protocols. Cross-protocol arbitrage opportunities. The complexity cascaded.
Yearn V2 launched in 2021. Up to 20 simultaneous strategies per vault. The basket now held multiple protocol positions, LP tokens, reward tokens, and leveraged positions across chains.
Three Data Problems Emerge
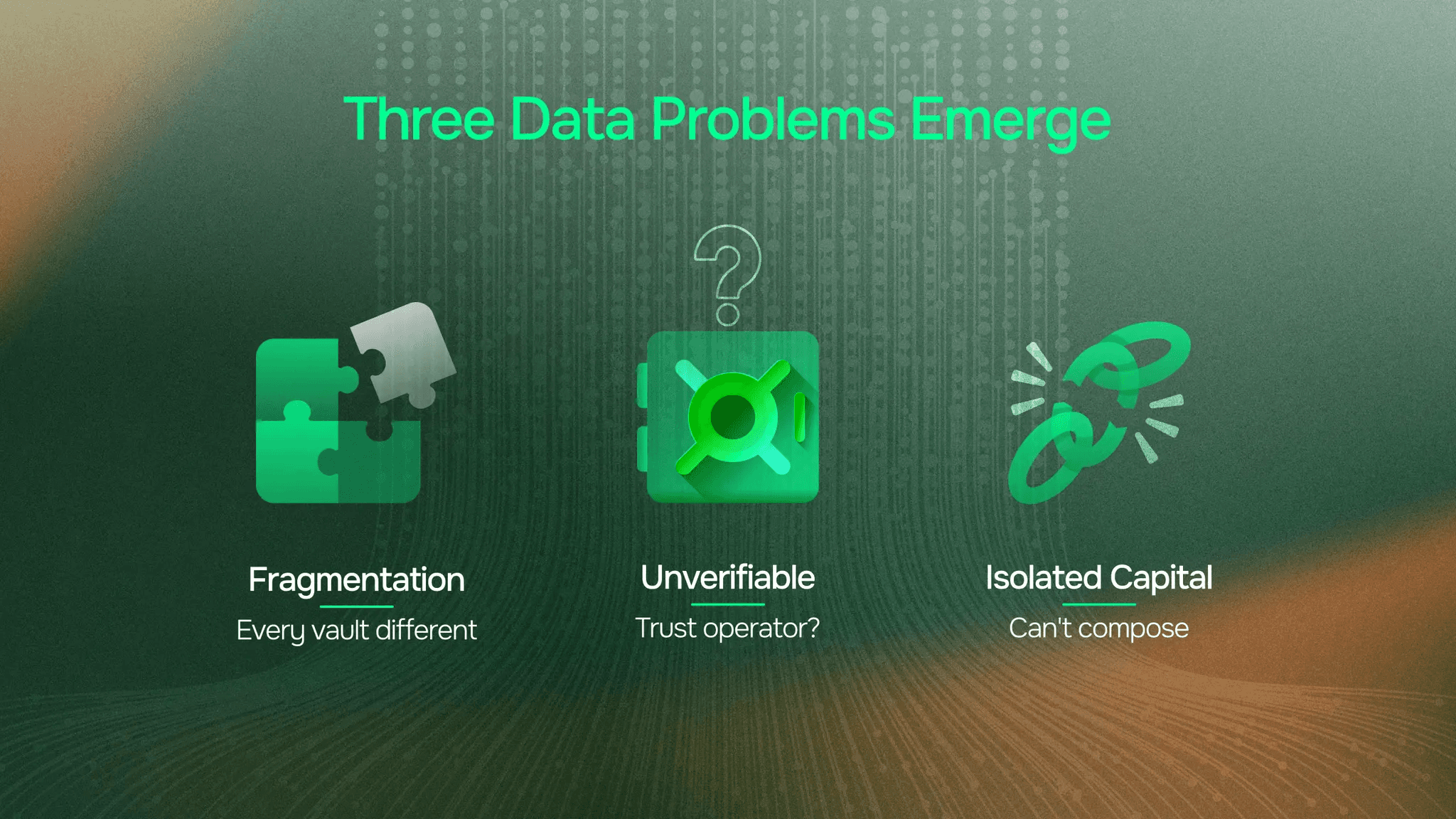
Problem 1: Fragmentation
Every vault calculated NAV differently. No common standard. Integration required custom adapters for each protocol. Developers couldn't build once and deploy everywhere. Each new vault meant new integration work.
Problem 2: Self-Reported Valuations (Unverifiable)
"This vault holds $100M across five protocols." Trust us?
Multi-protocol strategies made independent verification difficult. Users had no way to check complex positions without trusting the vault operator. The data existed on-chain, but aggregating it accurately required significant infrastructure.
Problem 3: Composability Breakdown
Lending protocols asked: "What's the liquidation value?" Unknown.
Risk managers asked: "What's the collateral worth?" Can't verify.
DEXs asked: "What's the fair price?" Unclear.
Vaults became isolated endpoints. Capital couldn't compose. The promise of DeFi as programmable building blocks hit a wall.
Oracle Risk Context
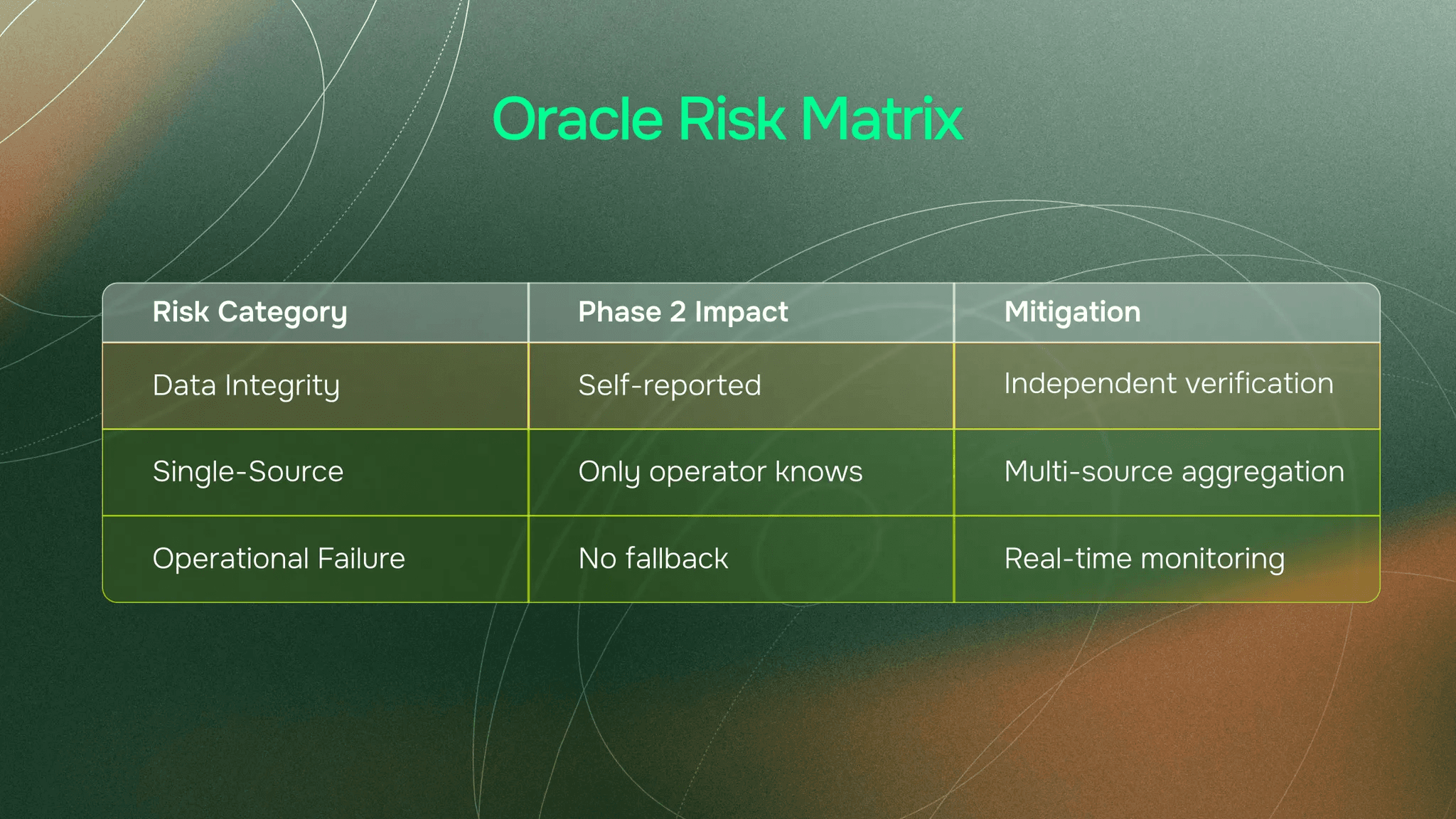
These issues map to specific oracle risk categories:
Data Integrity Risk: Self-reported valuations without verification meant no independent check on accuracy
Single-Source Risk: Only the vault operator knew true positions across protocols
Operational Failure Risk: No fallback if vault reporting broke during market stress
Even at this stage, the need for independent, verifiable data was clear. Vaults executing complex strategies across multiple protocols needed external verification that could track positions in real-time. Exactly what purpose-built oracle infrastructure provides.
Standardization arrived in 2022. But would it solve the verification problem?
Phase 3: Standardization Creates Verification Foundation (2022-2023)
ERC-4626 gave vaults a common language. Independent verification became possible. Composability unlocked.
ERC-4626: The Interface Standard
Finalized March 2022, ERC-4626 introduced a standardized interface for tokenized vaults. Standard methods: deposit(), withdraw(), totalAssets(), convertToShares().
Critical point: ERC-4626 became the dominant vault standard, though not universal. Most institutional-grade vaults adopted it because standardization enables composability. The difference between vaults isn't "type." It's the strategy they execute. Same interface, different approaches.
What Standardization Enabled for Data Infrastructure
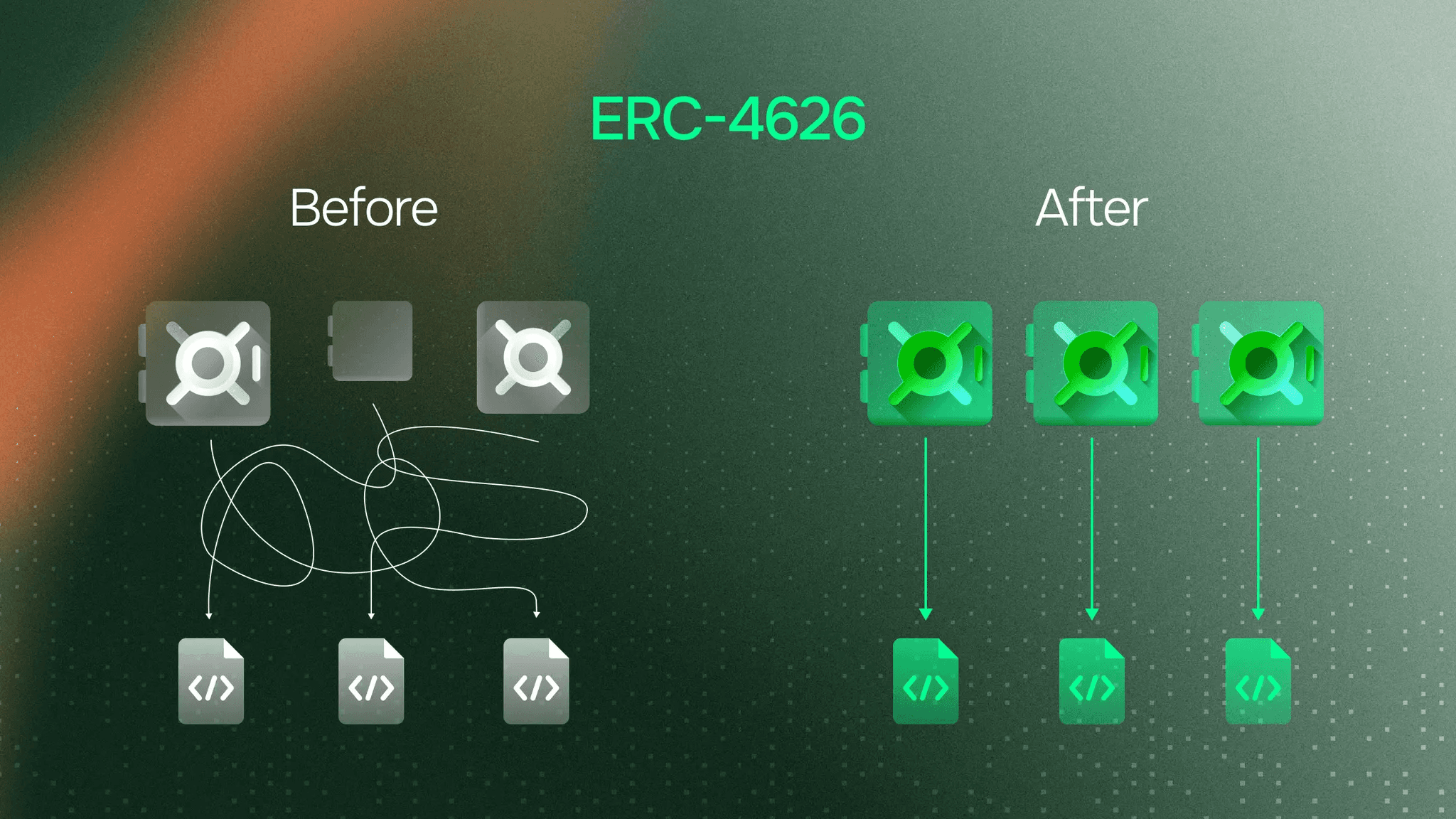
Independent verification:
Protocols could query vault contracts directly. Standard methods meant consistent calculations. Third-party analytics platforms (DefiLlama, Dune) could aggregate data uniformly across all compliant vaults.
Composability unlocked:
Vault tokens became usable as collateral. Morpho and Euler accepted ERC-4626 tokens in lending markets. "Vault-of-vaults" strategies emerged, with meta-vaults allocating across multiple underlying vaults. DEXs could price vault shares using standard conversion functions.
When On-Chain Calculations Aren't Enough
Phase 1 worked because everything was on-chain. Query Compound, calculate APY, done.
But as vaults evolved, the limitations became clear:
Multi-chain strategies emerged: A vault holds positions across Ethereum, Arbitrum, and Base. No single chain can see the full picture. Standard interfaces help, but cross-chain data aggregation requires specialized infrastructure.
Off-chain complexity arrived: RWA assets, external price sources, custodial holdings. On-chain contracts can't access this data directly. They need oracles to bring that information on-chain in a verifiable way.
This is where specialized oracle infrastructure becomes critical. When you need to aggregate data across chains or integrate off-chain information, you need infrastructure designed for that complexity.
ERC-4626 standardization created the foundation for specialized oracle infrastructure. The standard provided the interface; oracle networks like EO Network provide the verification. Independent NAV calculation. Stake-secured accuracy. Real-time updates that other protocols can trust.
As strategies grew more sophisticated, especially with curated vaults and flexible allocations, the need for dynamic data infrastructure became clear. Vaults change strategies daily. NAV feeds must update accordingly.
Curator-Managed Vaults Scale
Morpho and Euler introduced curator models: expert-managed strategies with on-chain accountability. Clear separation of roles: Owner, Curator, Allocator. Transparent decision trails.
Data implication: More complex positions requiring real-time monitoring. Curators need accurate data to manage risk. Lending protocols need that same data to evaluate collateral. Everyone depends on the data layer.
The Limitation
Standardization worked beautifully for crypto-native assets with on-chain price discovery. ETH, USDC, staked assets. All verifiable through existing infrastructure.
But what happens when the basket holds real-world assets?
RWA vaults expose where data infrastructure becomes foundational, not optional.
Phase 4: RWA Vaults Make Data Infrastructure Critical
Real-world assets create the most complex verification challenge. Off-chain value, on-chain representation. Purpose-built data infrastructure isn't optional here. It's foundational.
RWA Vault Strategies Redefine the Basket
What vaults now hold:
Tokenized Treasury securities. Private credit portfolios (Midas mF-ONE holds Fasanara fintech receivables). Real estate loans. Money market instruments.
The fundamental difference:
No on-chain price discovery. You can't check Uniswap to value a T-bill. The vault holds claims on off-chain value.
The Three Problems Return, Amplified
Challenge 1: Off-Chain Asset Opacity
How do you verify the vault actually holds what it claims?
Example: Midas mF-ONE holds private credit through Fasanara Capital's yield strategies, backed by a mix of off-chain assets ($148.71M, 99.88% of TVL) and on-chain liquidity buffers. A lending protocol needs to know: Do those assets exist? Are they performing? What's the real NAV?
Self-reported valuations don't work here. The data doesn't live on-chain.
Challenge 2: Institutional Requirements (Zero Trust Assumptions)
Regulated entities need auditable data trails. Independent verification, not vault operator attestation. Real-time NAV that accounts for off-chain asset performance.
"Trust the vault operator" isn't institutional-grade infrastructure. Institutions require verification.
Challenge 3: Composability Requires Trusted Data
Lending protocols won't accept RWA vault tokens as collateral without reliable NAV. Risk managers can't model exposure to assets they can't value independently. Capital remains siloed without verifiable data. The entire promise of composability breaks down.
Oracle Risk in RWA Context
RWA strategies carry High oracle risk severity because:
Off-chain valuations with centralized updates create data integrity risk
Assets aren't freely traded on-chain (no arbitrage mechanism to correct mispricing)
NAV calculation latency (hours to days for complex positions like private credit) creates exploitation windows
The Regulatory Dimension
RWA vaults often operate under regulatory frameworks requiring formal reporting. This creates both challenge and opportunity for data infrastructure.
The regulatory reality:
Many RWA assets come with compliance requirements. Tokenized securities, private credit funds, real estate. These aren't just DeFi experiments. They're regulated financial instruments.
What this means for data infrastructure:
Accurate NAV calculation depends on reliable source data. For RWAs, that data must meet regulatory standards. Audited valuations. Verified holdings. Documented methodologies.
The verification challenge:
Who verifies the verifiers? How do you ensure source data is accurate when it comes from off-chain custodians or asset managers?
How specialized oracle infrastructure addresses this:
Multiple data sources cross-reference valuations across independent providers. Multiple verification steps through layered checks before publishing on-chain. Distributed validator networks use broad consensus mechanisms to reduce single-point-of-failure risk.
The specifics are complex and vary by jurisdiction. But the principle is clear: regulated assets require regulated reporting, and oracle infrastructure must handle that complexity while maintaining decentralization.
The Data Infrastructure Solution
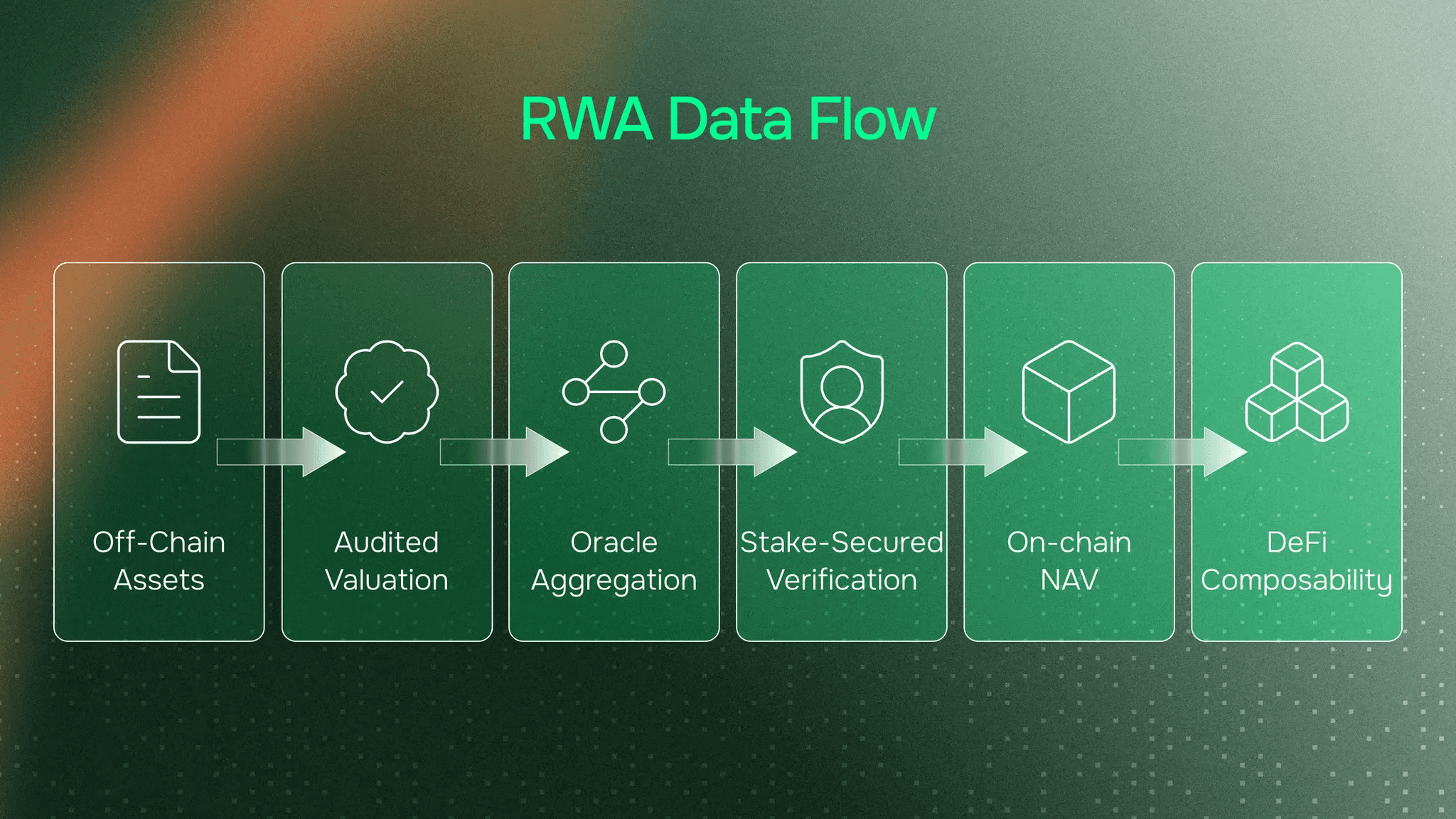
RWA vaults sit at the intersection of traditional finance regulation and DeFi composability. The data infrastructure must satisfy both worlds: traditional finance's auditable trails and verified sources, DeFi's on-chain delivery and trustless verification.
Here's how purpose-built infrastructure addresses this:
1. Independent NAV Verification (Not Self-Reported)
Third-party calculation from underlying positions. For off-chain assets: audited valuations, periodic appraisals. On-chain delivery where other protocols can read it.
Computational infrastructure: Complex positions like Midas mF-ONE require significant time to calculate accurately. Fasanara Capital updates NAV several times per week, reflecting the complexity of valuing private credit portfolios. This isn't instantaneous; it's deliberate and thorough.
2. Real-Time Flexibility
Critical insight: Vault strategies change frequently, daily or more. NAV infrastructure must adapt dynamically.
Example: A vault shifts from Treasuries to private credit. NAV calculation methodology changes. The oracle infrastructure must handle this flexibility without breaking composability.
3. Stake-Secured Accuracy
Data providers stake capital at risk. Bad data equals slashed stake. Economic incentives align with accuracy. This is how decentralized networks maintain trust without centralized authority.
4. Purpose-Built for Complexity
Generic price feeds don't work for RWA vaults. You need infrastructure designed for off-chain asset valuation, multi-source data aggregation with regulatory-grade verification, Proof of Reserve verification, and transparent calculation methodologies.
This is the infrastructure EO Network provides. Purpose-built for RWA vault complexity. NAV feeds that account for off-chain positions. Multi-source verification with distributed validator consensus. Stake-secured accuracy. Real-time updates that adapt as strategies change.
While ERC-4626 standardized the interface, oracle infrastructure like EO Network delivers the trusted data layer that makes RWA vaults composable. Not an add-on. Foundation.
Advanced Standards Enable Complex Strategies
ERC-7540 (Asynchronous): RWA assets require settlement time (T+1, T+2, longer). Request-based vaults formalize this: request withdrawal, wait for settlement, claim assets. Midas mF-ONE, for example, processes redemptions within 35 business days, reflecting traditional finance settlement cycles.
ERC-7575 (Multi-Asset): One vault accepts multiple assets (USDC, DAI, USDT). Critical for diversified strategies that need flexibility across stablecoin types.
Data implication: These standards formalize how to report pending transactions and multi-asset valuations. Infrastructure must support both asynchronous flows and multi-asset accounting.
Real-World Scale
Veda ($2B+ TVL):
Cross-chain vault strategies. Institutional-scale capital. Demonstrates that when data infrastructure is robust, complex strategies scale rapidly.
Upshift (Meta-Vault Example):
coreUSDC aggregates positions across multiple underlying vaults. Requires NAV aggregation in real-time. Shows how purpose-built infrastructure enables vault-of-vaults strategies that institutional investors demand.
Midas mF-ONE (RWA Pioneer):
Private credit vault with $148.89M TVL. NAV reflects off-chain loan performance through Fasanara Capital's strategies. Proof point: RWA infrastructure isn't theoretical. It's live.
Conclusion: Data Infrastructure as Foundation
Vaults evolved from simple auto-compounders to institutional infrastructure managing $27B+.
Each phase created new data requirements. Multi-protocol strategies caused fragmentation. Standardization built a verification foundation. RWA strategies demanded purpose-built infrastructure that bridges traditional finance regulation and DeFi composability.
We're at an inflection point. Institutions are entering. Infrastructure is catching up.
The pattern is clear: The vault is only as trustworthy as the data it runs on.
For RWA vaults bridging traditional finance and DeFi, data infrastructure isn't optional. It's foundational. Independent verification across multiple sources. Stake-secured accuracy. Real-time flexibility as strategies evolve. Regulatory-grade reporting delivered on-chain.
The buildout is already happening.
Explore how purpose-built oracle infrastructure enables institutional-grade vaults: docs.eo.app
Follow this series for technical deep dives on vault data infrastructure and live implementations.




